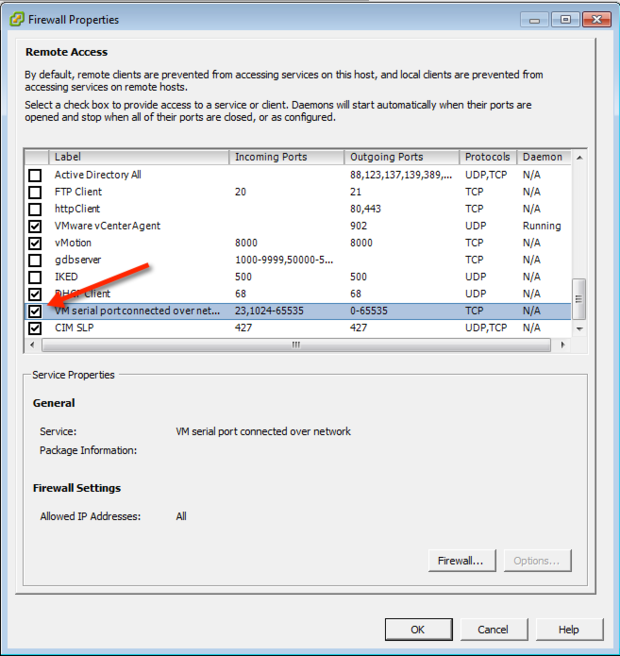
In today's digital landscape, VNC behind firewall has become a critical solution for businesses and individuals seeking secure remote access to their systems. As remote work continues to grow in popularity, understanding how VNC works within a firewall environment is essential for maintaining productivity while ensuring robust cybersecurity measures.
Virtual Network Computing (VNC) allows users to remotely control another computer as if they were sitting in front of it. This powerful tool has transformed the way we approach remote work, IT support, and system management. However, when firewalls are involved, special considerations must be taken to ensure seamless connectivity without compromising security.
This article delves into the intricacies of using VNC behind firewall, offering practical insights, best practices, and expert advice to help you navigate this complex setup. Whether you're a network administrator, IT professional, or an individual user, this guide will provide you with the knowledge needed to implement secure remote access solutions.
Read also:Albert Brown Iv A Comprehensive Look At His Life Achievements And Legacy
Table of Contents
- Introduction to VNC Behind Firewall
- Understanding the Basics of VNC
- What is a Firewall and Its Role in Network Security?
- Challenges of Using VNC Behind Firewall
- Solutions for VNC Behind Firewall
- Enhancing Security for VNC Behind Firewall
- Best Practices for Implementing VNC Behind Firewall
- Tools and Software for VNC Behind Firewall
- Case Study: Successful Implementation of VNC Behind Firewall
- The Future of VNC Behind Firewall
Introduction to VNC Behind Firewall
Why VNC Behind Firewall is Important
VNC behind firewall solutions are crucial for organizations that require secure remote access to internal systems while maintaining robust network security. Firewalls act as gatekeepers, controlling incoming and outgoing traffic to protect sensitive data. However, this protective mechanism can sometimes hinder the functionality of remote access tools like VNC.
By understanding how to configure VNC behind firewall, businesses can ensure that their employees and IT teams can access critical systems remotely without exposing the network to potential threats. This setup is particularly important for industries handling sensitive information, such as healthcare, finance, and government sectors, where compliance with data protection regulations is mandatory.
Understanding the Basics of VNC
What is VNC and How Does It Work?
Virtual Network Computing (VNC) is a graphical desktop sharing system that allows users to remotely control another computer over a network connection. It transmits keyboard and mouse input from the client to the server and displays the server's screen on the client's monitor. VNC operates on a client-server model, where the server is the machine being controlled, and the client is the machine initiating the connection.
VNC uses the Remote Framebuffer (RFB) protocol to transmit data between the client and server. This protocol is platform-independent, making VNC compatible with various operating systems, including Windows, macOS, and Linux. By leveraging VNC, users can access their workstations from anywhere in the world, as long as they have an internet connection and the necessary credentials.
What is a Firewall and Its Role in Network Security?
Firewalls as Network Security Gatekeepers
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks, such as the internet. Firewalls can be hardware-based, software-based, or a combination of both.
The primary function of a firewall is to prevent unauthorized access to or from a private network. It achieves this by filtering traffic, blocking specific IP addresses, and restricting access to certain ports and protocols. Firewalls are essential for protecting sensitive data and maintaining the integrity of a network. However, they can sometimes interfere with legitimate remote access tools like VNC, requiring careful configuration to ensure seamless connectivity.
Read also:How Many Points Does Experian Boost Give You A Comprehensive Guide
Challenges of Using VNC Behind Firewall
Common Issues and Obstacles
Implementing VNC behind firewall presents several challenges that must be addressed to ensure successful deployment. One of the primary issues is port blocking, as firewalls often restrict access to specific ports used by VNC for communication. Additionally, firewalls may block incoming connections from unknown sources, preventing remote users from establishing a connection.
Another challenge is ensuring secure authentication and encryption for VNC connections. Without proper security measures, sensitive data transmitted over VNC could be intercepted by malicious actors. Furthermore, network latency and bandwidth limitations can impact the performance of VNC connections, especially when accessing high-resolution graphics or running resource-intensive applications.
Solutions for VNC Behind Firewall
Configuring VNC to Work with Firewalls
To overcome the challenges of using VNC behind firewall, several solutions can be implemented. First, configure the firewall to allow traffic on the specific ports used by VNC, such as port 5900. This can be done by creating inbound and outbound rules that permit connections from trusted IP addresses or subnets.
Another solution is to use a reverse SSH tunnel to bypass firewall restrictions. This involves setting up an SSH connection from the server to the client, allowing the client to initiate a VNC connection through the established tunnel. Reverse SSH tunnels provide a secure and reliable method for accessing remote systems behind firewalls.
Enhancing Security for VNC Behind Firewall
Best Practices for Securing VNC Connections
Securing VNC connections is paramount when implementing VNC behind firewall. Start by using strong passwords and enabling two-factor authentication (2FA) to protect against unauthorized access. Additionally, encrypt VNC traffic using SSL/TLS or SSH tunneling to prevent data interception.
Limit access to VNC servers by configuring firewalls to allow connections only from trusted IP addresses or networks. Regularly update VNC software to ensure that security vulnerabilities are patched. Finally, monitor VNC activity logs to detect and respond to suspicious behavior promptly.
Best Practices for Implementing VNC Behind Firewall
Steps for Successful Deployment
When implementing VNC behind firewall, follow these best practices to ensure a successful deployment:
- Conduct a thorough risk assessment to identify potential security threats.
- Choose a VNC solution that supports advanced security features, such as encryption and authentication.
- Configure firewalls to allow only necessary traffic and block unauthorized access.
- Test the VNC setup in a controlled environment before deploying it in a production setting.
- Provide training and support to users to ensure they understand how to use VNC securely.
Tools and Software for VNC Behind Firewall
Popular VNC Solutions and Their Features
Several VNC solutions are available that offer features specifically designed for use behind firewalls. Some popular options include:
- TightVNC: A lightweight, open-source VNC solution that supports encryption and authentication.
- RealVNC: A commercial VNC product that offers enterprise-grade security and scalability.
- UltraVNC: A feature-rich VNC solution that includes file transfer and encryption capabilities.
- NoMachine: A remote access tool that provides high-performance VNC connections with advanced security features.
Case Study: Successful Implementation of VNC Behind Firewall
Real-World Example of VNC Behind Firewall
A large financial institution implemented VNC behind firewall to enable remote access for its IT support team. By configuring firewalls to allow traffic on specific VNC ports and using SSH tunnels for secure connections, the organization successfully deployed a VNC solution that met its security and performance requirements.
The implementation resulted in improved productivity, reduced downtime, and enhanced customer satisfaction. IT staff could quickly resolve issues without needing to be physically present at the client's location, saving time and resources. Furthermore, the secure VNC setup ensured compliance with industry regulations and protected sensitive financial data.
The Future of VNC Behind Firewall
Trends and Innovations in Remote Access Technology
As technology continues to evolve, the future of VNC behind firewall looks promising. Advances in encryption, authentication, and network protocols will enhance the security and performance of remote access solutions. Additionally, the rise of cloud-based VNC services offers new opportunities for scalable and flexible remote access deployments.
Organizations should stay informed about emerging trends and innovations in remote access technology to ensure they remain competitive and secure in an ever-changing digital landscape. By embracing these advancements, businesses can leverage VNC behind firewall to drive productivity, improve customer service, and maintain robust cybersecurity measures.
Conclusion
In conclusion, VNC behind firewall is a powerful solution for secure remote access that addresses the unique challenges of modern network environments. By understanding the basics of VNC, configuring firewalls appropriately, and implementing best practices for security and deployment, organizations can harness the full potential of this versatile technology.
We encourage readers to share their thoughts and experiences with VNC behind firewall in the comments section below. Additionally, explore other articles on our site to learn more about remote access solutions and network security. Together, let's build a safer and more connected digital world.