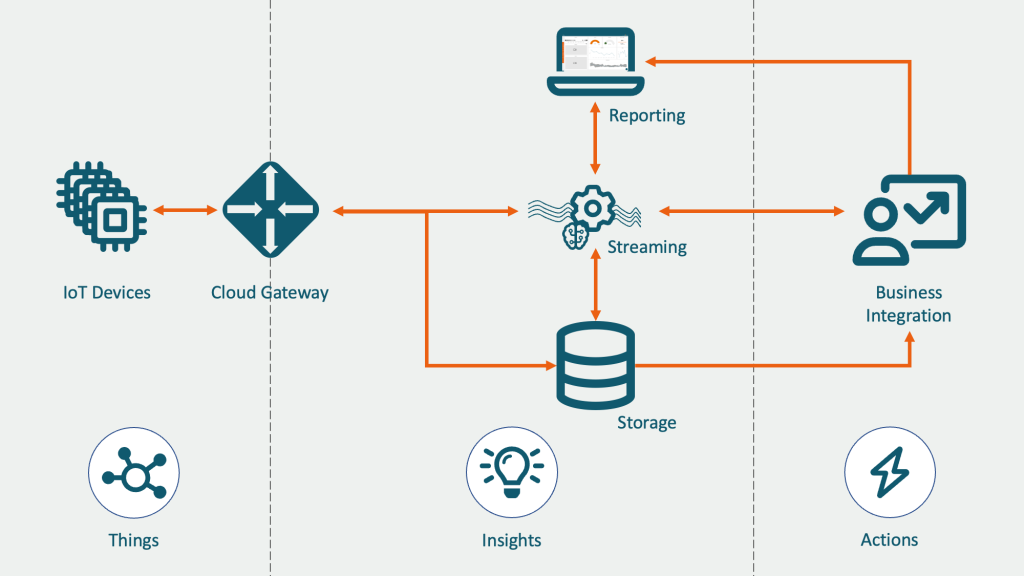
In today's interconnected world, understanding how to access IoT devices is crucial for both personal and professional use. The Internet of Things (IoT) has revolutionized the way we interact with technology, enabling seamless communication between devices and enhancing efficiency in various industries. As IoT continues to grow, it is essential to learn how to securely and effectively access these devices.
From smart homes to industrial automation, IoT devices are transforming the way we live and work. However, accessing these devices requires a solid understanding of the underlying technologies, security protocols, and best practices. In this comprehensive guide, we will explore everything you need to know about accessing IoT devices safely and efficiently.
This article will provide you with detailed insights into IoT device access, including practical tips, security considerations, and actionable advice. Whether you're a beginner or an experienced user, this guide will equip you with the knowledge to harness the full potential of IoT technology.
Read also:Noodles Magazine A Comprehensive Guide To The Worlds Premier Noodle Enthusiast Publication
Table of Contents
- Introduction to IoT Devices
- Methods to Access IoT Devices
- Securing IoT Device Access
- Common Challenges in IoT Access
- IoT Protocols for Device Access
- Tools for Accessing IoT Devices
- Best Practices for IoT Device Access
- Industries Using IoT Devices
- The Future of IoT Access
- Conclusion
Introduction to IoT Devices
IoT devices refer to any physical objects embedded with sensors, software, and connectivity features that allow them to exchange data with other devices and systems over the internet. These devices range from simple household gadgets like smart thermostats to complex industrial machinery equipped with advanced sensors and analytics capabilities.
The primary purpose of IoT devices is to enhance automation, improve decision-making, and streamline operations across various sectors. By connecting devices to the internet, users can remotely monitor, control, and manage them, leading to increased efficiency and cost savings.
Key Features of IoT Devices
- Connectivity: IoT devices are designed to communicate with other devices and systems via wireless or wired networks.
- Data Collection: These devices continuously gather data from their environment, providing valuable insights for analysis and decision-making.
- Automation: IoT devices can perform tasks automatically based on predefined rules or machine learning algorithms.
Methods to Access IoT Devices
Accessing IoT devices can be done through various methods, depending on the type of device and the intended use case. Below are some common methods for accessing IoT devices:
Remote Access
Remote access allows users to control and monitor IoT devices from a distance using a computer, smartphone, or tablet. This method is particularly useful for managing devices located in remote locations or monitoring multiple devices simultaneously.
Local Access
Local access involves interacting with IoT devices within the same network or physical proximity. This method is often used for configuring devices or troubleshooting issues on-site.
Securing IoT Device Access
Security is a critical consideration when accessing IoT devices. Due to the vast amount of data exchanged between devices, ensuring secure access is paramount to protect sensitive information and prevent unauthorized access.
Read also:Cloudysocial Customize Your Game Play Elevate Your Gaming Experience
Best Security Practices
- Use strong and unique passwords for all IoT devices.
- Enable encryption for data transmission between devices.
- Regularly update firmware and software to address security vulnerabilities.
According to a report by Gartner, the number of IoT devices worldwide is expected to reach 25 billion by 2030, highlighting the growing need for robust security measures.
Common Challenges in IoT Access
While IoT devices offer numerous benefits, accessing them can present several challenges. Some of the most common challenges include:
Interoperability Issues
Different IoT devices often use varying communication protocols and standards, making it difficult to ensure seamless integration and access across platforms.
Network Congestion
As the number of connected devices increases, network congestion can become a significant issue, leading to slower performance and reduced reliability.
IoT Protocols for Device Access
Several communication protocols are used to facilitate the interaction between IoT devices. Understanding these protocols is essential for effective device access. Some of the most widely used IoT protocols include:
MQTT (Message Queuing Telemetry Transport)
MQTT is a lightweight protocol designed for low-bandwidth environments, making it ideal for IoT applications. It supports publish/subscribe messaging patterns, enabling efficient communication between devices.
CoAP (Constrained Application Protocol)
CoAP is a specialized web transfer protocol designed for resource-constrained devices. It is based on the HTTP model but optimized for low-power environments.
Tools for Accessing IoT Devices
Various tools and platforms are available to simplify the process of accessing IoT devices. These tools provide users with intuitive interfaces and advanced features for managing and monitoring their devices.
Popular IoT Platforms
- Amazon Web Services (AWS) IoT
- Microsoft Azure IoT
- Google Cloud IoT
These platforms offer scalable solutions for deploying, managing, and securing IoT devices, catering to a wide range of industries and use cases.
Best Practices for IoT Device Access
To ensure optimal performance and security when accessing IoT devices, it is essential to follow best practices. Below are some key recommendations:
Regular Maintenance
Perform regular maintenance tasks, such as firmware updates and system checks, to keep your IoT devices running smoothly.
Monitor Device Activity
Keep track of device activity to detect any anomalies or unauthorized access attempts promptly.
Industries Using IoT Devices
IoT devices are utilized across various industries to enhance operations and improve efficiency. Some of the key sectors leveraging IoT technology include:
Healthcare
In the healthcare industry, IoT devices are used for remote patient monitoring, telemedicine, and medical equipment management.
Manufacturing
Manufacturers employ IoT devices for predictive maintenance, quality control, and supply chain optimization.
The Future of IoT Access
The future of IoT access looks promising, with advancements in technology paving the way for more sophisticated and secure interactions between devices. Emerging trends such as edge computing and artificial intelligence are expected to play a significant role in shaping the evolution of IoT access.
As IoT continues to expand, the demand for innovative solutions to address security and interoperability challenges will grow, driving further development in the field.
Conclusion
Understanding how to access IoT devices is essential for maximizing the benefits of this transformative technology. By following the methods, protocols, and best practices outlined in this guide, you can securely and effectively interact with IoT devices in various applications.
We invite you to share your thoughts and experiences with IoT device access in the comments section below. Additionally, feel free to explore other articles on our site for more insights into the world of IoT and related technologies.