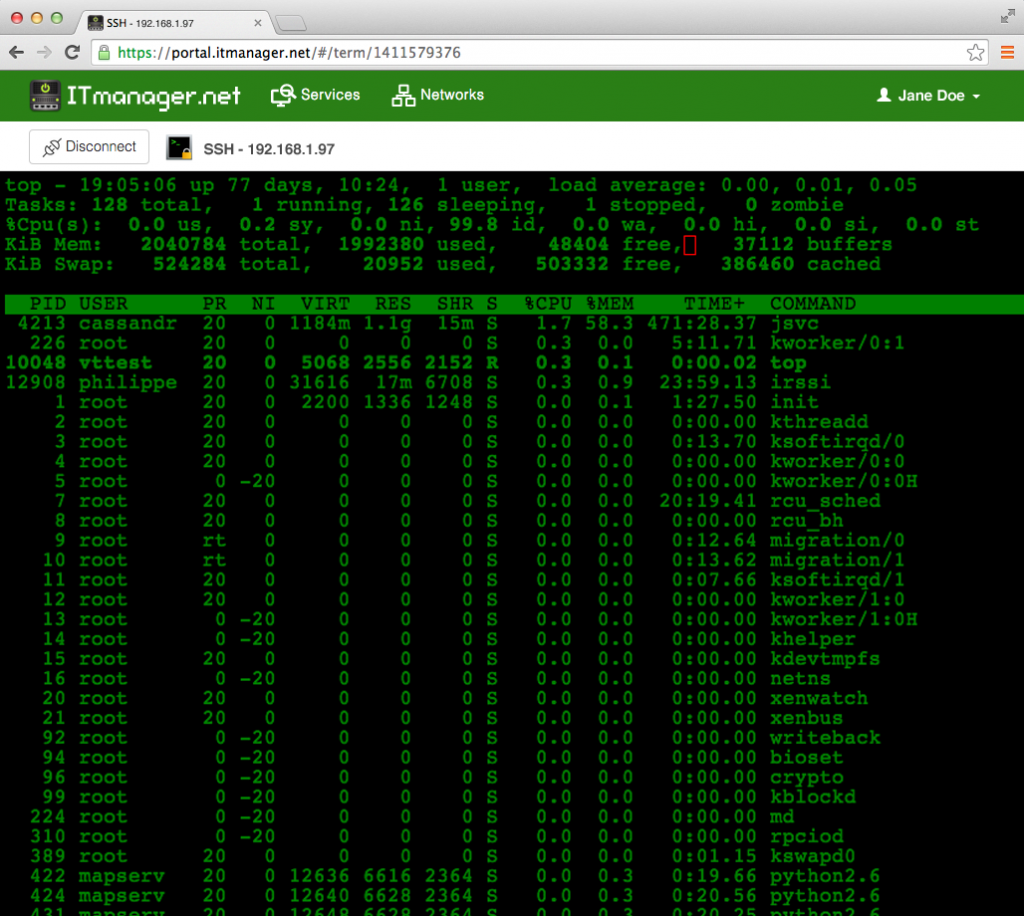
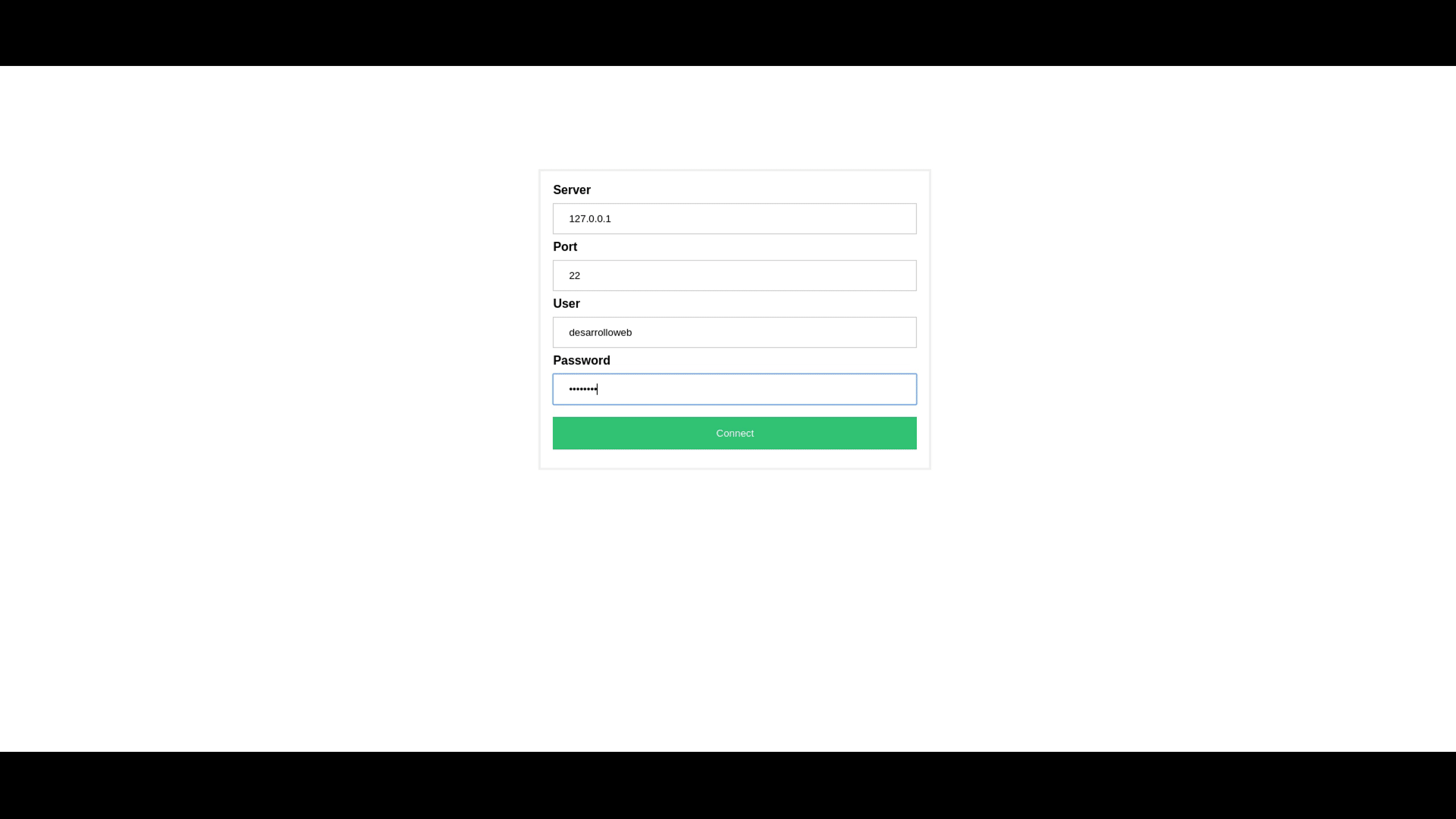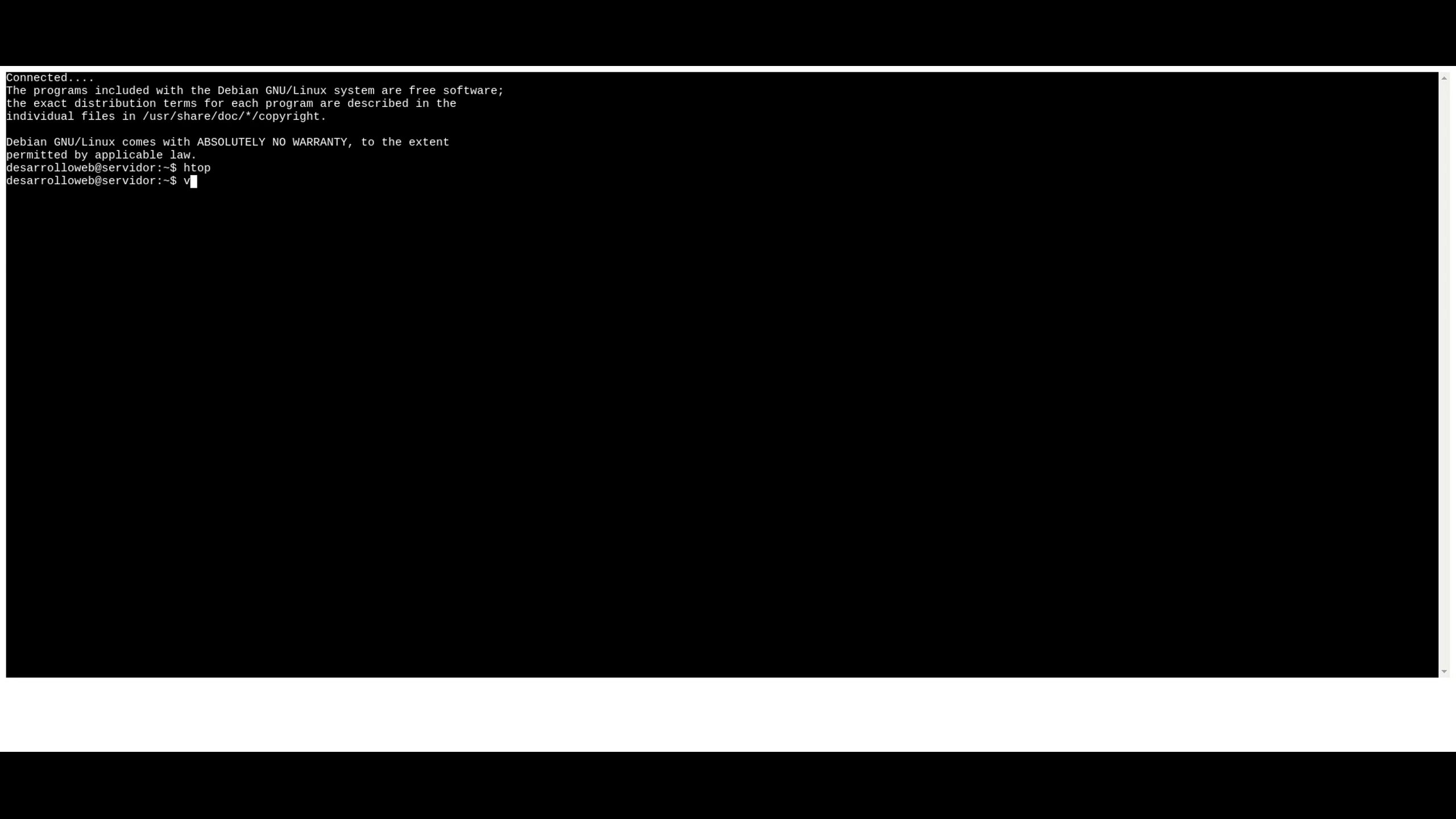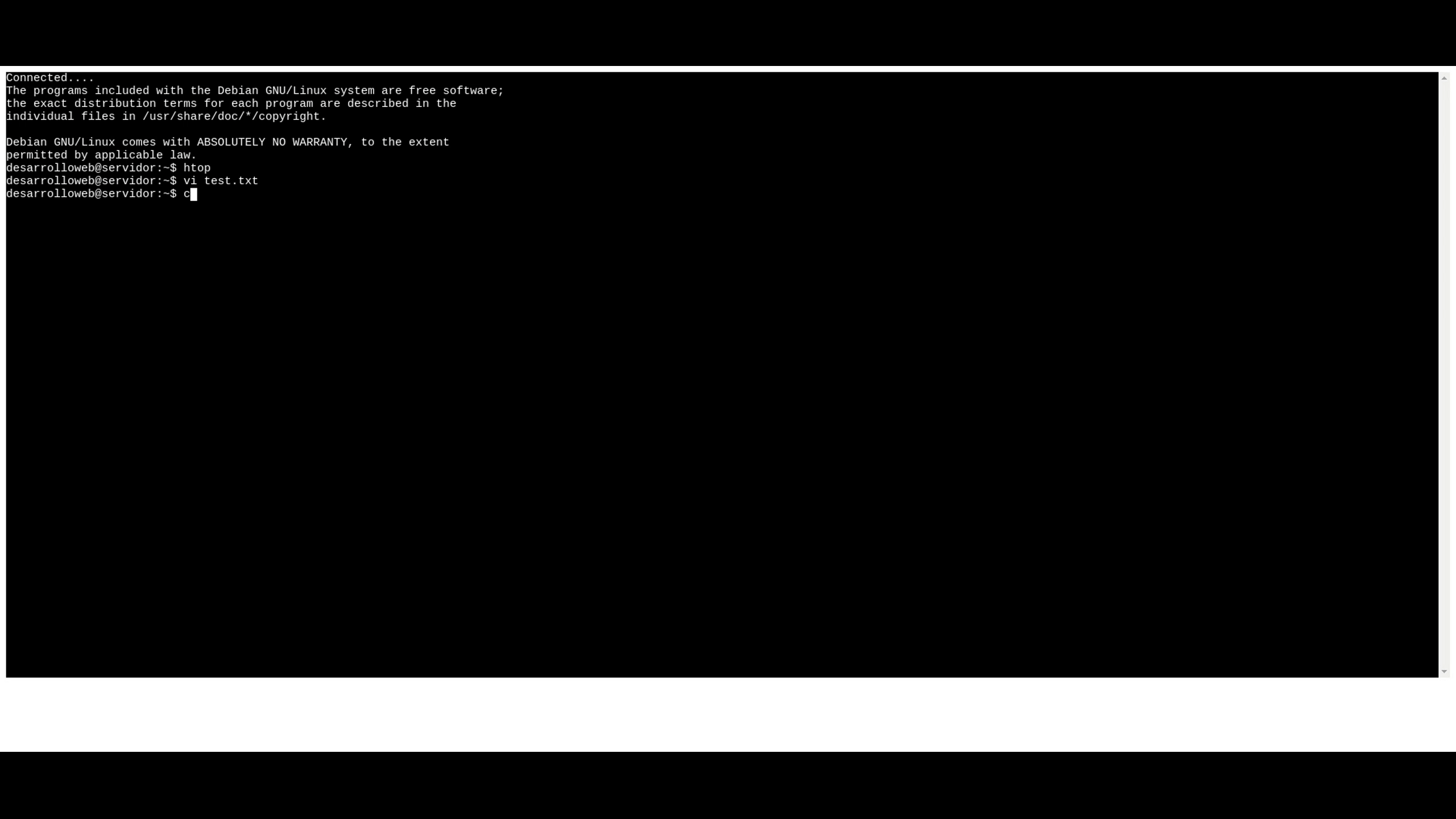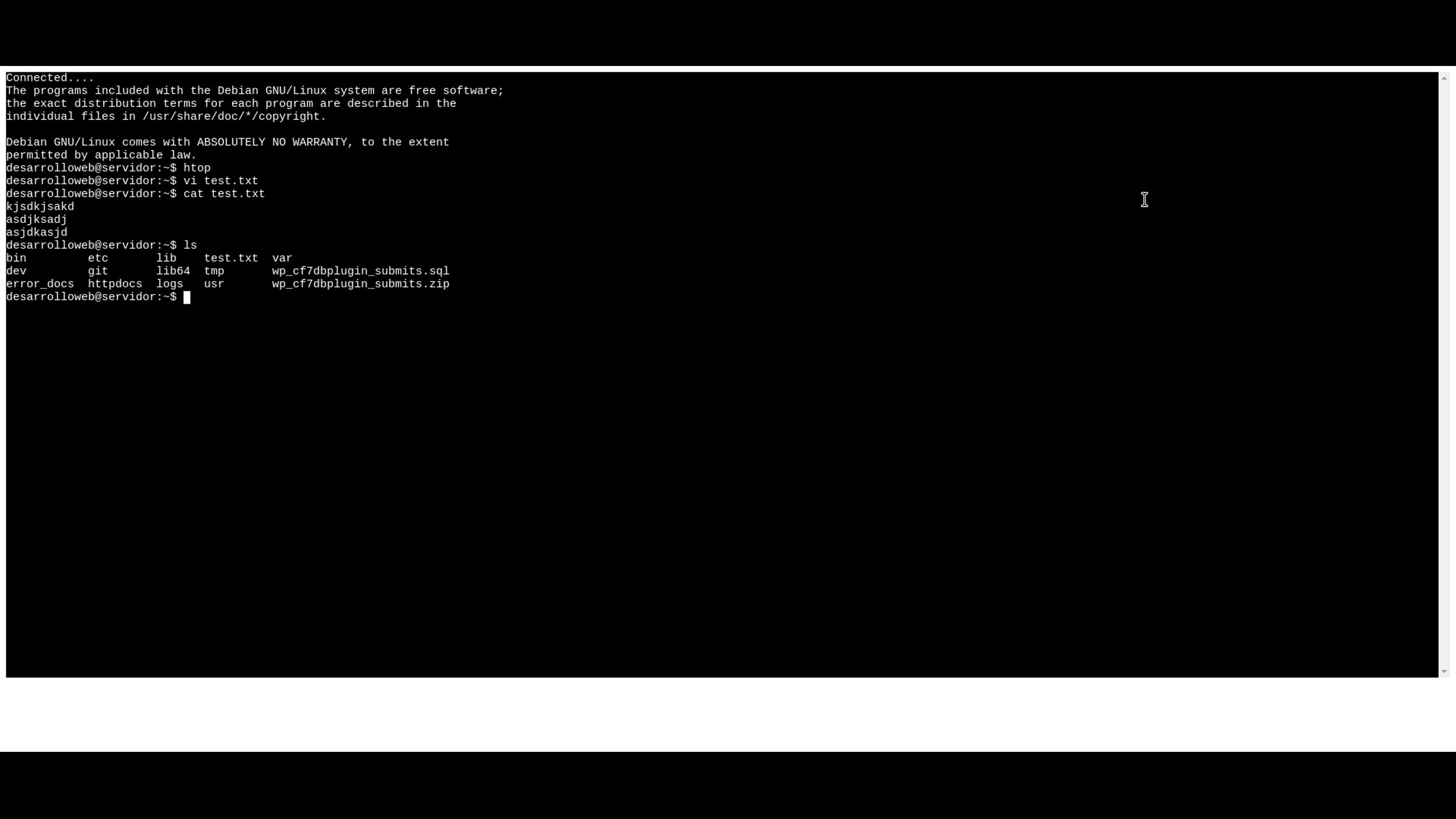
In today's digital age, remote IoT web SSH has become a crucial component for businesses and individuals looking to manage their IoT devices securely and efficiently. The ability to access and control devices remotely through secure shell (SSH) protocols opens up a world of possibilities. Whether you're a tech enthusiast or a business owner, understanding remote IoT web SSH is essential for optimizing your operations.
With the rapid expansion of the Internet of Things (IoT), the need for secure and reliable remote access solutions has never been greater. RemoteIoT web SSH offers a secure way to connect to devices from anywhere in the world, ensuring that your systems remain protected while maintaining optimal performance.
This comprehensive guide will walk you through everything you need to know about remote IoT web SSH, including its benefits, implementation, and best practices. By the end of this article, you'll have a solid understanding of how to leverage this technology to enhance your IoT infrastructure.
Read also:Daria Sergeyevna Gordeevagrinkova A Detailed Exploration Of Her Life And Achievements
Table of Contents:
- What is RemoteIoT Web SSH?
- Benefits of RemoteIoT Web SSH
- How to Implement RemoteIoT Web SSH
- Ensuring Security with RemoteIoT Web SSH
- Tools and Platforms for RemoteIoT Web SSH
- Common Challenges and Solutions
- Best Practices for RemoteIoT Web SSH
- The Future of RemoteIoT Web SSH
- Frequently Asked Questions
- Conclusion
What is RemoteIoT Web SSH?
RemoteIoT web SSH refers to the process of remotely accessing IoT devices using Secure Shell (SSH) protocols via a web interface. This method allows users to securely connect to their devices from any location with an internet connection, providing a seamless experience for managing and monitoring IoT infrastructure.
SSH, originally developed as a network protocol for secure data communication, has become a cornerstone of remote access solutions. By combining SSH with web-based interfaces, RemoteIoT web SSH offers an intuitive and secure way to interact with IoT devices without the need for complex setups or additional software installations.
Key Features of RemoteIoT Web SSH
- Encrypted communication between devices and users.
- Web-based interface for easy access.
- Support for multiple devices and platforms.
- Real-time monitoring and control capabilities.
Benefits of RemoteIoT Web SSH
Implementing RemoteIoT web SSH offers numerous advantages for both individuals and organizations. Below are some of the key benefits:
Read also:Kimberly Violette Petty The Rising Star Shaping The Entertainment Industry
1. Enhanced Security
SSH protocols provide robust encryption and authentication mechanisms, ensuring that your IoT devices remain secure from unauthorized access. This is particularly important in an era where cyber threats are becoming increasingly sophisticated.
2. Flexibility and Convenience
With RemoteIoT web SSH, you can access your devices from anywhere in the world using a web browser. This eliminates the need for physical presence and allows for more flexible management of IoT infrastructure.
3. Cost Efficiency
By leveraging web-based SSH solutions, organizations can reduce the costs associated with traditional remote access methods, such as dedicated hardware or proprietary software.
How to Implement RemoteIoT Web SSH
Implementing RemoteIoT web SSH involves several steps, including setting up the necessary infrastructure and configuring the devices. Below is a step-by-step guide to help you get started:
Step 1: Choose the Right Platform
Select a platform or service that supports RemoteIoT web SSH. Some popular options include OpenSSH, WebSSH, and cloud-based solutions like AWS IoT Core.
Step 2: Configure SSH on Your Devices
Ensure that SSH is enabled on your IoT devices and properly configured with strong authentication methods, such as public key authentication.
Step 3: Set Up a Web Interface
Use a web-based SSH client or integrate a web interface into your existing infrastructure to enable remote access via a browser.
Ensuring Security with RemoteIoT Web SSH
Security is a top priority when implementing RemoteIoT web SSH. Here are some best practices to ensure your system remains protected:
- Use strong passwords and enable two-factor authentication (2FA).
- Regularly update your devices and software to patch vulnerabilities.
- Limit access to authorized users only and monitor activity logs.
- Implement firewalls and intrusion detection systems to enhance security.
According to a report by Cisco, the number of IoT devices is expected to reach 75 billion by 2025, highlighting the importance of secure remote access solutions. [Source: Cisco]
Tools and Platforms for RemoteIoT Web SSH
Several tools and platforms are available to facilitate RemoteIoT web SSH. Below are some of the most popular options:
1. OpenSSH
OpenSSH is an open-source SSH protocol implementation that supports secure remote access. It is widely used and highly customizable.
2. WebSSH
WebSSH provides a web-based interface for accessing SSH-enabled devices. It is easy to use and requires no additional software installations.
3. AWS IoT Core
AWS IoT Core is a managed cloud service that enables secure communication between IoT devices and the cloud. It supports SSH and offers advanced features like device management and analytics.
Common Challenges and Solutions
While RemoteIoT web SSH offers numerous benefits, there are some challenges to consider. Below are some common issues and their solutions:
Challenge 1: Connectivity Issues
Solution: Use reliable internet connections and implement failover mechanisms to ensure uninterrupted access.
Challenge 2: Security Threats
Solution: Follow best practices for securing SSH connections, such as enabling encryption and using strong authentication methods.
Challenge 3: Scalability
Solution: Choose a platform that supports scaling to accommodate growing IoT infrastructure needs.
Best Practices for RemoteIoT Web SSH
To maximize the effectiveness of RemoteIoT web SSH, consider the following best practices:
- Regularly audit and update your security policies.
- Train employees on secure remote access procedures.
- Document all configurations and settings for future reference.
- Test your system regularly to identify and address potential issues.
The Future of RemoteIoT Web SSH
As the IoT landscape continues to evolve, RemoteIoT web SSH is expected to play an increasingly important role in managing and securing IoT devices. Advancements in technology, such as quantum encryption and artificial intelligence, will further enhance the capabilities of remote access solutions.
According to a study by Gartner, by 2025, 60% of enterprises will adopt cloud-based IoT management solutions, underscoring the growing demand for secure and scalable remote access technologies. [Source: Gartner]
Frequently Asked Questions
Q: Is RemoteIoT web SSH secure?
A: Yes, RemoteIoT web SSH is secure when properly configured and implemented using best practices.
Q: Can I use RemoteIoT web SSH on mobile devices?
A: Yes, many web-based SSH clients are compatible with mobile devices, allowing you to access your IoT devices on the go.
Q: What are the main advantages of using RemoteIoT web SSH?
A: The main advantages include enhanced security, flexibility, and cost efficiency.
Conclusion
RemoteIoT web SSH is a powerful tool for managing and securing IoT devices remotely. By understanding its benefits, implementation, and best practices, you can optimize your IoT infrastructure and ensure its long-term success.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT and related technologies. Together, let's build a safer and more connected world!